By Alexandru Voica, Imagination Technologies
Last week I had the pleasure of attending the official launch of the IoT Security Foundation. Held on the top floor of the Digital Catapult building in central London, this event included speakers from Beecham Research, NMI, Copper Horse, and Imagination Technologies.
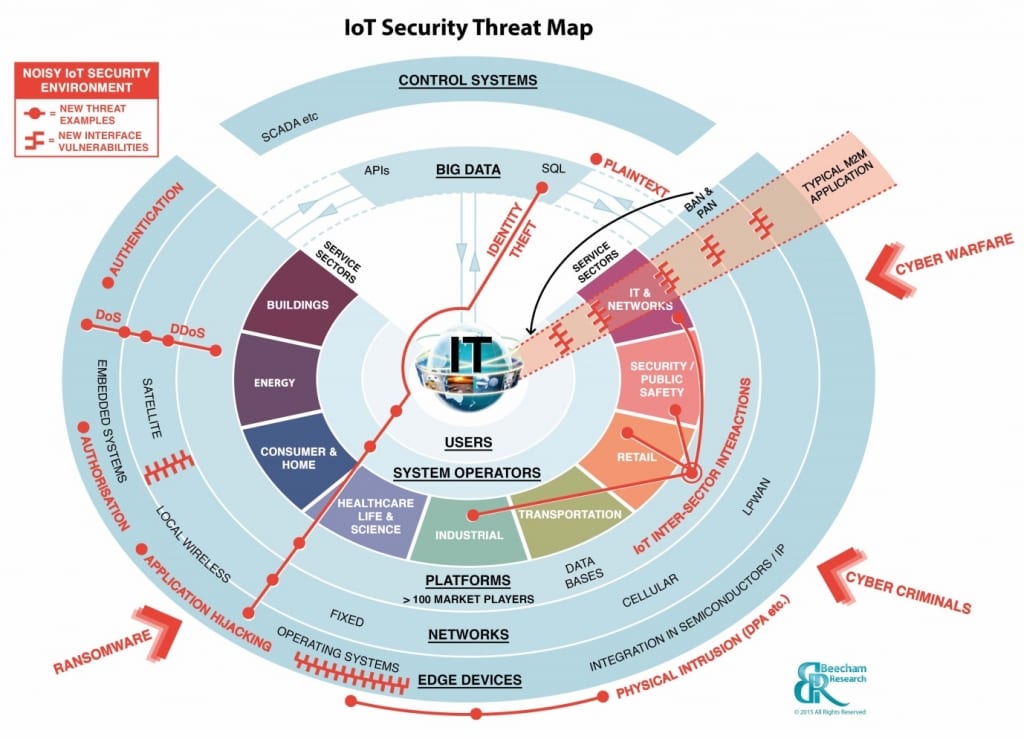
Robin Duke-Woolley, CEO of Beecham Research, set the scene by introducing the IoT security threat map below. Reviewing the different attack points highlighted on the diagram, Duke-Woolley remarked how the IoT market would have to face a significantly larger number of threats than the traditional M2M sector.
The connected devices market is set to explode by 2020, with annual shipments of over five billion devices and a growth rate close to 50%.
This is because M2M platforms tend to focus on specific applications where potential breach attempts are usually a known quantity. On the other hand, the IoT market is open to many companies building disparate technologies and products that need to work together. The problem facing IoT developers is the lack of uniformity across the different common layers and interfaces used to build Internet-connected devices; this in turn hinders the development of a cross-platform security strategy among various IoT companies, institutions or foundations.
Robin Duke-Woolley concluded that maintaining heightened security in the fast growing IoT market requires a new game plan.
A new security paradigm
NMI chairman Stan Boland was up next talking about the current state of IoT security and what needs to change in the future. Boland talked about an IoT v1.0 that includes disjointed silos of smart sensors transmitting data to gateways and data centers which then use machine learning and other intelligent processing technologies to store and process information.
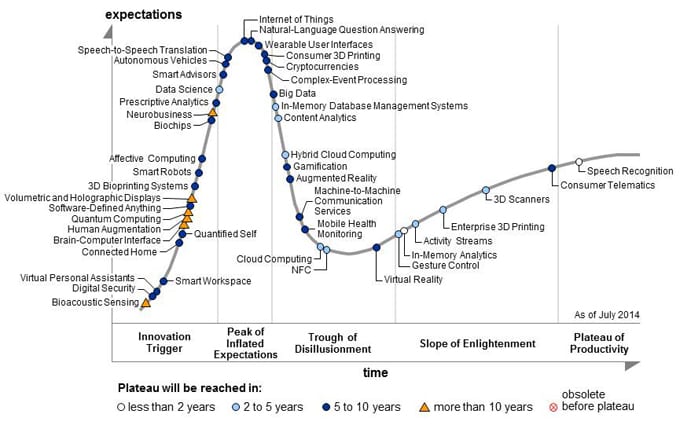
IoT entered the Gartner hype cycle in 2011 and has stayed on top of the curve for the last two years
This approach works fine for small sets of data that are processed locally or independently but fails to scale to truly connected platforms where interoperability is a key concept.
John Moor, VP of new segments at NMI, then stepped up to introduce the IoT Security Foundation. Initially chaired by leading security experts from UK companies and institutions, the Foundation ultimately aims to be a global organization building a top to bottom security framework for connected devices.
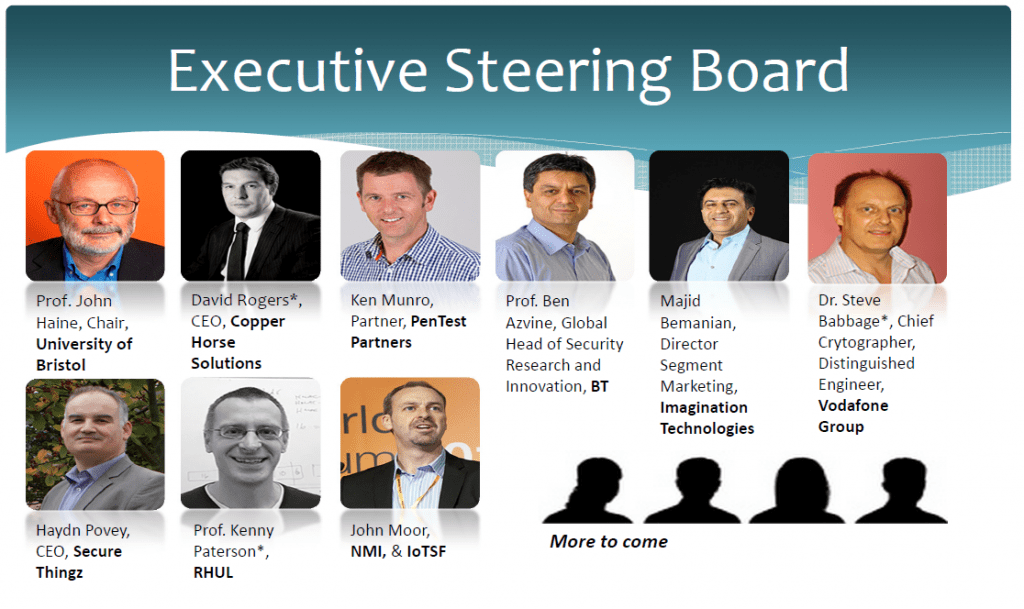
Leading security experts sit on the executive board of the Foundation
Moreover, the IoT Security Foundation is an inclusive forum that doesn’t focus on a specific category of companies, but includes everyone in the manufacturing chain (IP providers, semiconductor designers, OEMs and ODMs, operators or retailers).
The Foundation aims to promote excellence in IoT security
Members of the Foundation will be working to provide a holistic approach to security best practices and a cohesive strategy that addresses wide-ranging concerns from multiple stakeholders.
After the Second World War, airline companies worked together to convince the public it was safe to fly. The mission of the IoT Security Foundation is to make it safe to connect.
Finally, Imagination CEO Hossein Yassaie took the stage to offer his valuable insight about how companies worldwide tackle security in the hyper-connectivity age. Many players in the IoT market view security and reliability as closely related concepts; for example, hacking a connected car turns it into liability both for the person behind the wheel and for other drivers on the road. Therefore, it is important that companies designing IoT devices must start implement virtualized-based security at the hardware level to add a further level of protection and reliability against attacks or failures.
Sir Hossein Yassaie wrapped up his speech by declaring the IoT Security Foundation officially open for business to the applause of the audience.
I’m really excited to see the Foundation being announced and can’t wait to see it taking an active role in the development of security guidelines for the next generation of IoT devices.
Stay tuned to our blog and follow us on social media for more updates coming soon!
About Alexandru Voica
 After having experienced the fast-paced world of the IP business as a junior engineer at various companies around Europe, Alexandru Voica has decided to pursue his dream of working in technology marketing and PR for Imagination Technologies. His background includes research in computer graphics at the School of Advanced Studies Sant’Anna in Pisa and a brief stint as a CPU engineer. When not planted firmly in front of his laptop, Alexandru can be found hitting the basketball court, singing along at a rock n’ roll concert, enjoying art cinema or reading his favorite American authors. You can follow him on Twitter @alexvoica.
After having experienced the fast-paced world of the IP business as a junior engineer at various companies around Europe, Alexandru Voica has decided to pursue his dream of working in technology marketing and PR for Imagination Technologies. His background includes research in computer graphics at the School of Advanced Studies Sant’Anna in Pisa and a brief stint as a CPU engineer. When not planted firmly in front of his laptop, Alexandru can be found hitting the basketball court, singing along at a rock n’ roll concert, enjoying art cinema or reading his favorite American authors. You can follow him on Twitter @alexvoica.