By Hongmei He, Manufacturing Informatics Centre, Cranfield University, MK43 0AL.
Cranfield University is a Founder Member of IoTSF
Internet of Things (IoT) technology has enabled the fourth industrial revolution (Industry 4.0) by connecting factories and plants to the Internet. “Smart Factory” is connected with supply chains through the Internet. Data flows from machines and the factory floor to the Cloud, and subsequent information exchanges occur between all stakeholders in a supply chain. This enables synchronised and concerted control in all aspects of manufacturing, offering an easier, smarter, more productive and more prosperous manufacturing processes lifecycle with real-time information and real-time management[1].
However, the increasing use of the Internet and mobile devices means that modern manufacturing systems also face vulnerabilities and threats from the Internet (Fig. 1).
Fig. 1 Evolution from legitimate to modern manufacturing systems1
Inadequately protected networks, processes and operations pose huge threats to industrial plants and businesses. They are open to a range of attacks and cybercrimes, and threatened by interference, disruption or denial of process controls, theft of intellectual property, the loss of sensitive corporate data, hostile alterations to data, and industrial espionage. Once attackers gain access to a critical application, they can manipulate machines or manufacturing processes remotely.
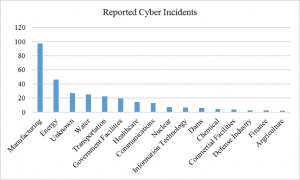
Modern manufacturing systems are less secure than traditional manufacturing systems, and cyber threats to the Industrial IoT are global and growing[1]. Automotive manufacturers were on the top of targeted manufacturing, accounting for almost 30% of the total attacks against the manufacturing industry in 2015, according to IBM3. This was demonstrated in 2010 when the computer worm Stuxnet sabotaged an Iranian uranium enrichment infrastructure, and in 2014 when cyber criminals manipulated and shut down the furnace of a German steelworks[2]. The US Department of Homeland Security has identified the manufacturing sector as the leading target of infrastructure cyber-attacks, accounting for one third of total attacks [3] (Fig. 2).
Fig. 2 US Reported Cyber Incidents by Critical Infrastructure Sector4.
Security challenges in legitimate manufacturing systems
Most industrial environments were not designed with cybersecurity in mind. Manufacturing systems are now moving from closed systems into IP-based cyber-physical systems, at which vulnerabilities are created. This is exacerbated because legitimate manufacturing components communicate with specific protocols within an industry network.
These protocols define data exchanges between controllers and peripheral devices as well as parameter setting and diagnosis. They are not well secured against cyber-threats in modern networked environments and hacking technology becomes increasingly sophisticated alongside IT advances.
It is now possible to attack a connected automatic car through channels such as Bluetooth, WiFi, Cellular or cloud, and directly interfere with the car’s control systems. In the automotive industry focus is starting to shift from the physical protection of vehicles, drivers and passengers to protection against cyber-attacks and intrusions1. Protection of legitimate manufacturing systems is a critical challenge when they are connected to the Internet.
To mitigate cyber-threats to legitimate manufacturing systems, it is vital that manufacturing operators’ security awareness is strengthened – as well as reinforcing security software and systems- people are inherently considered the weakest link1.
Increased mobility and under-administrated BYODs also offer attackers opportunities to target organisations through their employees. Regular training could improve employees’ security awareness and update their skills for cybersecurity.
Organisations need to implement basic controls against common cyber-threats, such as those specified by the UK government (www.cyberaware,gov.uk/cyberessentials). There is also a need to create security regulation through developing security metrics in terms of manufacturing special security objectives. Comprehensive security metrics, covering management, operation and technical metrics, can ensure specific security objectives are put into place, and drive an organisation to improve its overall security.
Security by design in smart manufacturing
Companies need to update their existing IT security if they want to benefit long-term from Industrie 4.0 and create a competitive advantage. Traditional security tools against traditional threats remain indispensable, and need to adapt to growing digitisation and be supplemented by new, innovative methods of defence[1].
One approach of defence is to insert security measures into application programmes, known as “Security by Design”. It should strengthen single applications and embedded systems and enable them to self-protect against tampering, reverse-engineering, and malware insertion.
A recent solution, the prplSecurity Framework, developed by prpl foundation[2], implements a prplHypervisor™ to isolate a controller/CPU with peripherals, such as Ethernet/SPI, prplPUFTM API, and USB/UART. This type of isolator could protect manufacturing systems from attacks.
Another solution could be online detection of threats, using machine learning for cybersecurity[3]. Recently, Symantec has launched Endpoint Protection Suite, using advanced machine learning, in three versions for SMEs, enterprises and managed service providers[4]. It can be installed at client site. But, can we design it inside the manufacturing systems?
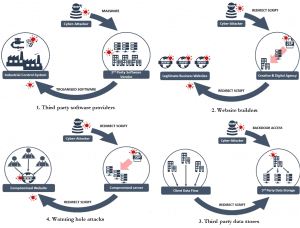
Researchers1 in cybersecurity for manufacturing have analysed horizontal and vertical data flows. Information exchanges in the horizontal data flow (i.e. supply chains) and the vertical data flow (i.e. IT stack) form an IoT data network. Due to different security levels in supply chain, it could become an important channel to attack enterprise and manufacturing systems. Identified cyber-risks include Trojan, malware, botnet and water holes[5] (Fig. 3). The complexity of the IoT data network creates a critical challenge for data protection – making data protection a major task in cybersecurity for the manufacturing sector.
Fig. 3 Identified risks in supply chains9.
If all production process applications could intelligently detect threats and defend themselves against attacks, manufacturing systems would be strongly secured. However, this would add a high overhead to systems performance and could affect the accessibility of critical data, running time and robust security controls. This could lead to faulty production or production rejects. Therefore, a secure IoT architecture is demanded to protect smart manufacturing, and manufacturing QoS should be standardised.
Education Demand
Higher education is a major contributor to economic success, producing, changing and transferring cutting edge knowledge from research. This requires us to continue updating our education to match the pace of technology development. Industrie 4.0 is promoting traditional manufacturing towards smart manufacturing with advanced IT technology. To promote the success of smart manufacturing, there is a huge demand of professionals with expertise in advanced technologies, such as IoT, Big Data, Cloud Computing and Cyber Security. Cranfield University will launch an MSc course in Cyber-Secure Manufacturing in October 2017, addressing those topics above. This course combines the two domains of advanced IT and manufacturing, and aims to develop the next generation of manufacturing engineers/managers who are able to protect manufacturing systems & machines against cyber threats[1].
The objective is to enable students to use cutting-edge technologies to (i) identify cyber threats in manufacturing systems from the Internet/cloud; (ii) protect manufacturing systems from cyber-attacks; (iii) improve incident response and disaster recovery in manufacturing systems; (iv) assess the cost of cybersecurity solutions for manufacturing systems.
[1] H. He, T. Watson, C. Maple, A. Tiwari, J. Mehnen, Y. Jin, B. Gabrys, The Security Challenges in the IoT enabled Cyber-Physical Systems and Opportunities for Evolutionary Computing & Other Computational Intelligence, WCCI2016, Vancouver, Canada, 24-29 July, 2016
[2] M. Albert, Seven things to know about the internet of things and industry 4.0. Modern Machine Shop Magazine, 88(4):74, Sept 2015.
[3] http://www.iottechnews.com/news/2016/jul/01/why-industry-40-manufacturing-needs-be-better-prepared-cyber-attacks/
[4] Ian Wright, Manufacturing Sector Identified as Leading Target of Infrastructure Cyber-Attacks, posted on 09 May 2016. http://www.engineering.com/AdvancedManufacturing/ArticleID/12050/Manufacturing-Sector-Identified-as-Leading-Target-of-Infrastructure-Cyber-Attacks.aspx, accessed on 7 Dec 2016.
[5] Mirko Brandner, From Production Slumps to Industrial Espionage: Why the Manufacturing Sector Must Be Better Prepared for Cyber Attacks, Tuesday, July 12, 2016. www.infosecisland.com/blogview/24786-From-Production-Slumps-to-Industrial-Espionage-Why-the-Manufacturing-Sector-Must-Be-Better-Prepared-for-Cyber-Attacks.htmlAccessed, 07/12/2016.
[6] Cesare Garlati, In Silicon We Trust: How to Fix the Internet of Broken Things, IoTSF Conference, 6 Dec 2016.
[7] H. He, A. Tiwari, J. Mehnen, T. Watson, C. Maple, Y. Jin, B. Gabrys, Incremental Information Gain Analysis of Input Attribute Impact on RBF-Kernel SVM Spam Detection, WCCI2016, Vancouver, Canada, 24-29 July, 2016.
[8] Semantec SPOTLIGHT: Defining the Future of Cyber Security, London, 1 Dec. 2016
[9] CERT-UK. Cyber-security risks in the supply chain. www.cert.gov.uk/wp-content/uploads/2015/02/Cyber-security-risksin-the-supply-chain.pdf, Feb 2015.
[10] Course Specification for MSc in Cyber-Secure Manufacturing, Manufacturing Department, Cranfield University, approved in July 2016.
Disclaimer:
The views and opinions expressed in this article are those of the authors and do not necessarily reflect the official policy or position of the IoT Security Foundation.