A blog post by John Moor
The State of Vulnerability Disclosure in Global Consumer IoT just got its eighth annual check-up – and the results are, well, encouraging yet sobering.
Published this month (January 2026) by Copper Horse Ltd in partnership with the IoT Security Foundation, the report ‘The State of Vulnerability Disclosure Policy Usage in Global Consumer IoT in 2025’ tracks how well manufacturers of internet-connected devices are making it possible for researchers to report security flaws.

Now in its 8th year, this longitudinal series remains the global reference for measuring real-world adoption of vulnerability disclosure policies (VDPs) in the consumer IoT space.
The Headline Progress: Slow but Steady Climb
After years of slow gains, the 2025 data shows meaningful forward movement:
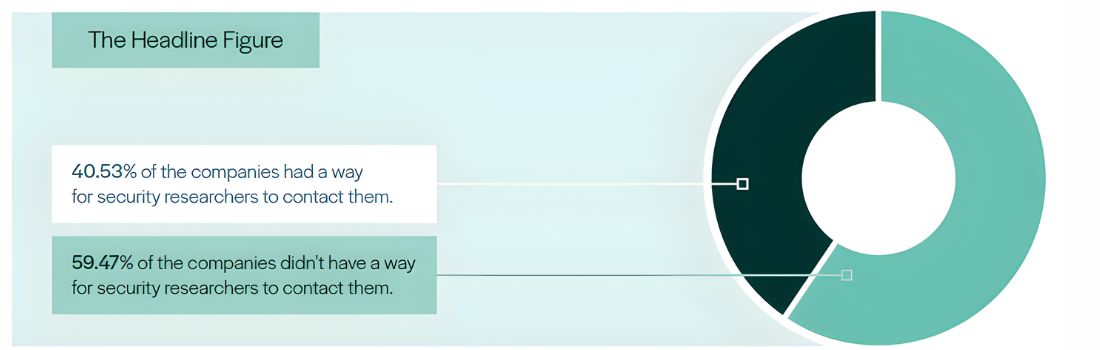
– 40.53% of the 491 manufacturers in the dataset now provide a way for security researchers to contact them about vulnerabilities. That’s a +4.94% improvement over the 2024 figure (35.59%)
– Yet 59.47% still offer no public contact method at all – meaning most consumer IoT products remain in the dark when it comes to open channels for reporting and coordinated disclosure
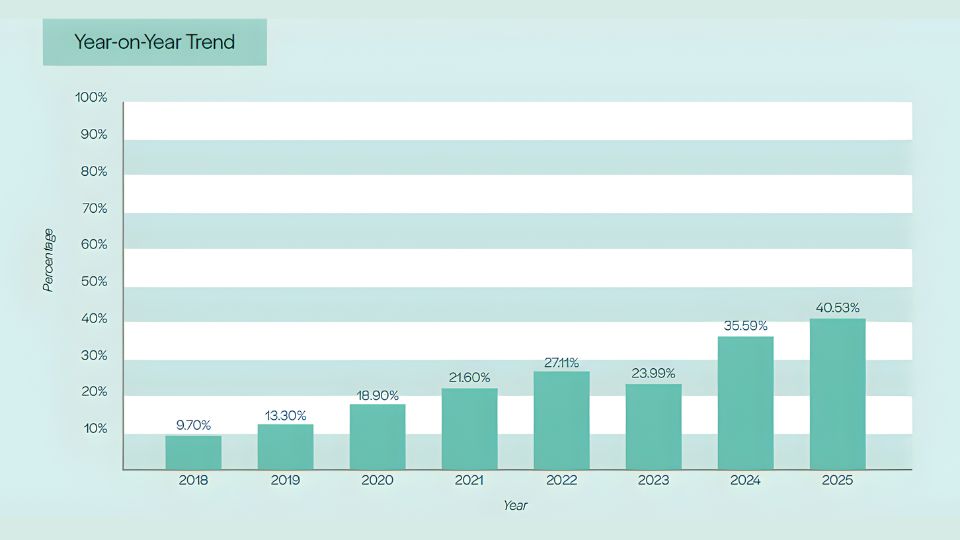
The year-on-year trend tells the story clearly: adoption has risen consistently since the research began, but we’re still far from the near-100% coverage that regulators (and common sense) demand in an era of widespread connected devices.
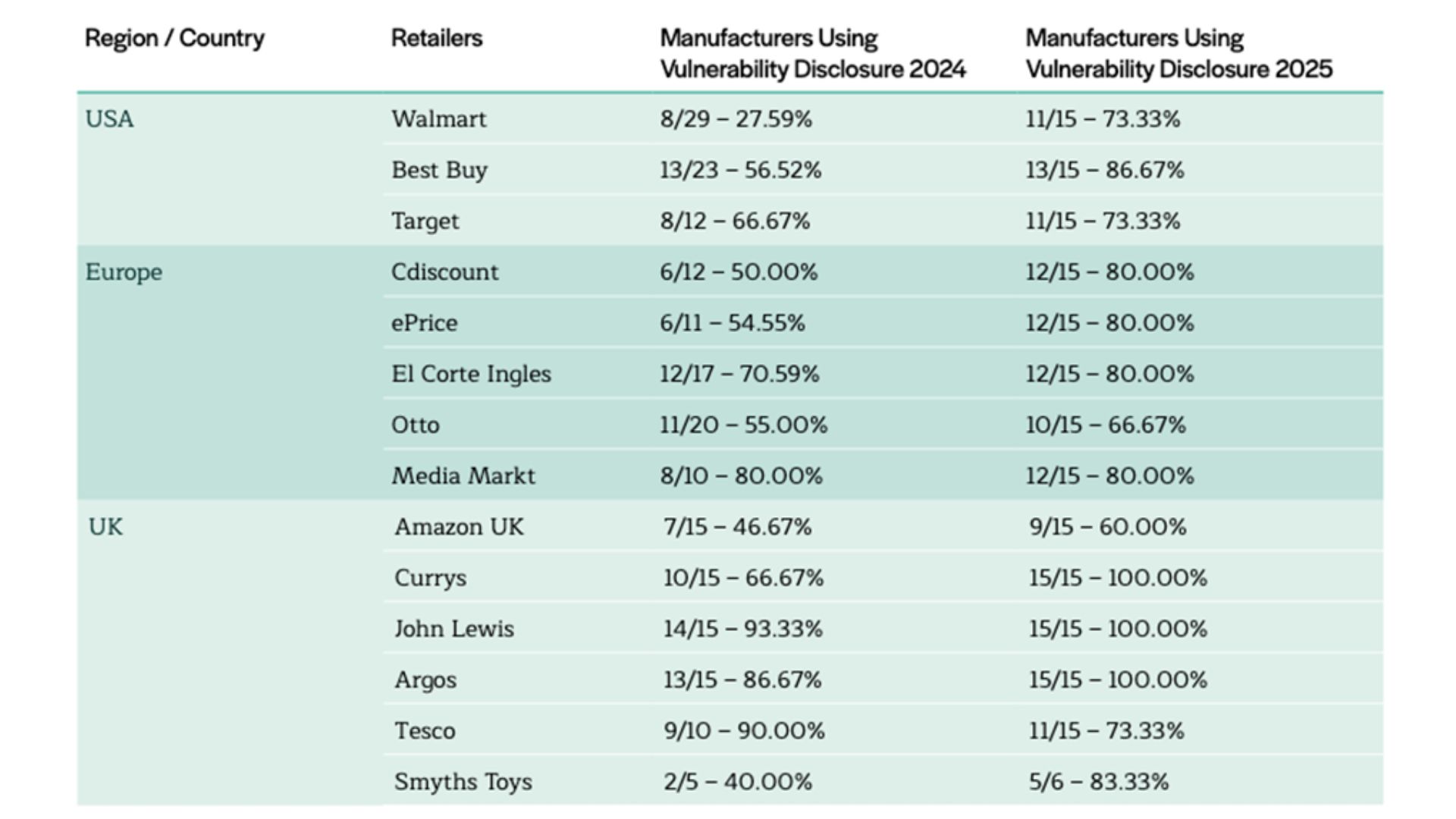
Retailer Dip Test: Where Regulation Really Bites
One of the most positive signals comes from the retailer sampling (‘dip test’) of popular IoT products:
– Across 15 major global retailers, nearly all now show >60% of sampled popular manufacturers with a VDP
– Nine out of 15 retailers hit >80%
– Three UK retailers achieved 100% adoption among the popular IoT products they stock
Clear rules + enforcement = tangible results
This is not a coincidence – it’s the direct impact of the UK’s PSTI regulations (in force since April 2024), which require clear vulnerability disclosure mechanisms and transparency on security support periods.
Why This Matters Right Now (Regulatory Clock is Ticking)
The timing couldn’t be more critical:
– The EU Cyber Resilience Act (CRA) entered into force in December 2024. Mandatory reporting of actively exploited vulnerabilities (tight 24/72-hour windows) kicks in from September 2026, with full obligations (including long-term security support) arriving in December 2027
– Australia’s Cyber Security (Security Standards for Smart Devices) rules take effect from March 2026 – mandating effective disclosure channels
– The US FCC IoT Cybersecurity Labelling Program and similar moves elsewhere add global pressure
Manufacturers without structured disclosure processes aren’t just behind best practice – they’re increasingly exposed to regulatory risk, market surveillance, and researcher/public scrutiny.
However, the report highlights significant industry confusion and concern over how the CRA intersects with traditional best practices like Coordinated Vulnerability Disclosure (CVD):
- Terminology overlaps create mix-ups: The CRA uses ‘disclosure of vulnerabilities’ for mandatory reporting to authorities (e.g., to the European vulnerability database), which clashes with the security community’s long-established meaning of disclosure (researcher → manufacturer → eventual public release after patching)
- Draft standards (e.g. prEN 40000-1-3 on vulnerability handling) entangle researcher reporting with supply-chain elements like SBoMs, introduce subjective terms like ‘responsible’ disclosure (historically problematic), and allow loopholes (e.g. accepting generic customer service contacts as sufficient)
- Experts consulted during research expressed no common view on expectations, with some fearing the compliance-heavy approach could complicate agile handling, diminish the researcher’s role, and discourage collaboration
These issues risk undermining the trust and efficiency of CVD – a proven, researcher-endorsed process that protects users by catching issues early without immediate public exposure.
The report calls for clearer nomenclature (e.g. ‘share vulnerability information’ for authority reporting), better alignment with existing international standards, and guidance from bodies like ENISA to resolve the confusion before deadlines bite.
The report also flags emerging challenges: new sales channels like TikTok Shop and influencer commerce blur accountability lines, while smaller/newer vendors continue to lag badly.
Bottom Line & Next Steps
The direction of adoption is upward – more brand-name manufacturers and retailers are treating vulnerability disclosure as a value signal rather than a regulatory checkbox. But with over half the market still absent to researchers, the gap between compliance and true commitment remains wide.
This unique 8-year dataset is essential reading for anyone in IoT product development, security research, regulation, retail, or policy.
Download the full report for free
Get the complete figures, regional breakdowns, product category insights, observations on security.txt usage, response efficiency, smart watch manufacturers, and much more (including discussion of the CRA standards for vulnerability disclosure).
