
Aligns with forthcoming standards and makes improvements of use
Today, the IoT Security Foundation (IoTSF) announced the availability of the latest release of its popular IoT Security Compliance Framework. The Framework is intended to be used by professionals that design, specify and procure IoT related products by providing guidance and easy to use questionnaire.
First published in December 2016, the Framework has evolved based on feedback and is now at Release 2.1 with recent efforts focussed on improving the practical usability of the questionnaire, alignment to the forthcoming ETSI EN 303 645 standard and changes to clarify the type of evidence expected for each security requirement.
Ease of Use for Audits
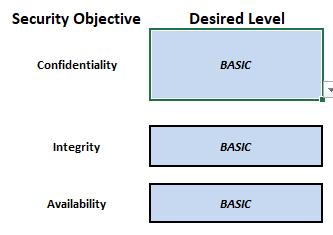
The comprehensive coverage of requirements, combined with its flexibility of use, makes the Framework an authoritative and versatile tool. With simplicity in mind, users can configure security requirements by selecting their desired objectives which are determined by selecting the confidentiality-integrity-availability intent. The tool then auto-determines which requirements are necessary to achieve a compliance-class level with space provided to record evidence of compliance. In this way, the Framework becomes an index to organisational documents as auditable proof for IoT security. This simplifies the management and maintenance of cybersecurity.
A spokesperson for the Working Group said “A key goal for this release was to improve the practical usability, the logical flow and transparency of the Framework. During the process of updating the questionnaire, formula-based automation has been added to help filter and auto populate many of the requirement entries. The mechanisms are fully transparent and open to inspection.”
John Moor, Managing Director of IoTSF said “The IoT Security Compliance Framework is one of our most popular publications with over 5000 being downloaded across the globe by industry since March 2019. We have been told by users that they often make use of it to support their internal process and as an authoritative reference guide. Its popularity may be because it has been produced by the same type of professionals that need to use it – so it is both a comprehensive and user-friendly tool. We now encourage all IoT vendors to download the latest version and make good use of it.”
More about the Framework as Tool
The Framework can be used internally in an organisation to self-assess or self-certify against, or by a third-party auditor. It can also be used ‘in part’, as a procurement mechanism to help specify security requirements of a supplier contract. The scope of the Framework includes (but is not limited to):
- Business processes
- The ‘Things’ in IoT i.e. Network connected products and/or devices
- Aggregation points such as gateways and hubs that form part of the connectivity
- Networking including wired, and radio connections, Cloud and server elements
Providing good security capability requires decisions upfront in design and use – often referred to as ‘secure-by-design’. In most cases, addressing the security of a product at the design stage is proven to be lower cost, and requiring less effort than trying to “put security” into or around a product after it has been created (which may not even be possible). Decisions need to be made to address use-case, business model, liability level and risk management in addition to technical concerns such as architecture, design features, implementation, testing, configuration and maintenance.
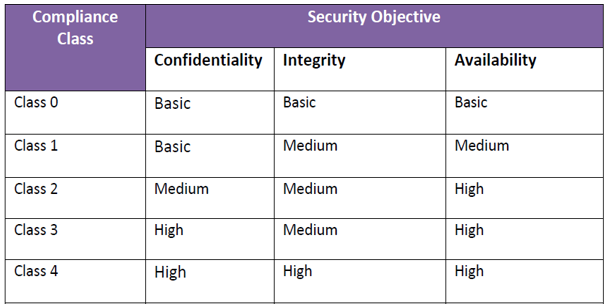
Cybersecurity requirements vary widely depending on the intended use case, context of application, system design and products used. As such, the Framework adopts a risk based approach to guide users and defines five classes (0-4) to help users understand the increasing risks that security measures need to mitigate.
All end-use products are constructed using a set of component parts, typically sourced from a variety of suppliers. These parts may be electronic or mechanical components, software modules or packages, including open source. Many of these parts will be procured from third party suppliers and it is important that all elements, together with the supply chain logistics, be subject to a security review/audit.
The IoT Security Compliance Framework breaks the process down and leads its user through a structured process of questioning and evidence gathering. The evidence gathered during the process can be used to declare conformance with best practice to customers and other stakeholders.
The latest version of the Framework is available free to download without registration from the IoT Security Foundation website from the links in the sidebar or at https://iotsecurityfoundation.org/best-practice-guidelines


