Internet of Things Security Foundation Joins Hacking Community at Blackhat and DEF CON conferences in Las Vegas
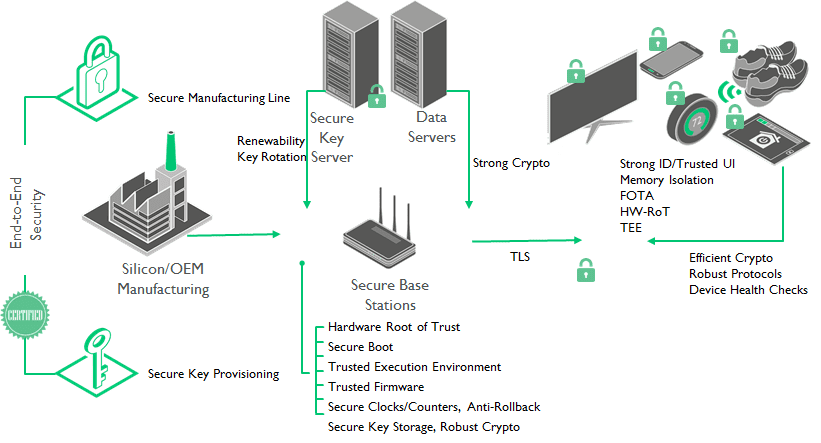
Seeks reviewers for security best practice guidelines Release Date: July 28th 2016 Two board directors and security expert members from the IoT Security Foundation (IoTSF) will be seeking input from hackers and security researchers at Blackhat and DEF CON 24 for best practice guidance documentation during the first week of August: Analysts agree that the